Difference between revisions of "3rd Party VMS/Milestone/Setup IVS Rules"
| Line 12: | Line 12: | ||
===Description=== | ===Description=== | ||
| − | This article shows how to set up an Intrusion rule in Milestone with a DH-IPC-HDW44A1MN. | + | This article shows how to set up an Intrusion rule in Milestone with a DH-IPC-HDW44A1MN-I. |
Please make sure that the camera already has an Intrusion or Tripwire rule setup on the camera before continuing to Milestone. | Please make sure that the camera already has an Intrusion or Tripwire rule setup on the camera before continuing to Milestone. | ||
Revision as of 22:55, 9 February 2018
Contents
How to Setup IVS Rules in Milestone
Compatible Devices
- N68BR4V using firmware: DH_IPC-HX8XXX-Nova2_Eng_P_Stream3_V2.622.0000001.4.R.171107
- 49225TNI using firmware: DH_SD-Mao-Rhea_EngSpnFrn_N_Stream3_IVS_V2.600.0000.2.R.20170905.zip
- N25BB5Z using firmware: DH_IPC-HX5X3X-Rhea_EngSpnFrn_N_Stream3_V2.622.0000000.18.R.20171110.zip
- X58A3 using firmware(MOTION DETECTION ONLY): DH_HCVR8xxx_EngSpnFrn_NP_V3.218.0000.0.R.20170613
- DH-IPC-HDW44A1MN-I using firmware: IPC-HX4X2X-Themis EngSpn N Stream3 V2.600.0005.0.R.20161219.zip]
Description
This article shows how to set up an Intrusion rule in Milestone with a DH-IPC-HDW44A1MN-I.
Please make sure that the camera already has an Intrusion or Tripwire rule setup on the camera before continuing to Milestone.
NOTE: Intrusion and Tripwire are the only two rules working in Milestone as of current testing.
Prerequisites
- Device with IVS Features
- IVS rule already setup in the device
- XProtect Management Client
Video Instructions
Step by Step Instructions
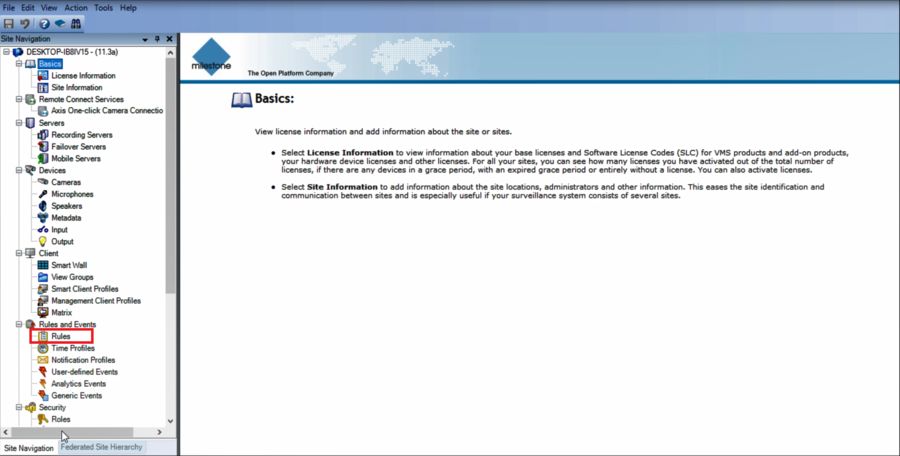
1. Open XProtect Management Client and go to Rules
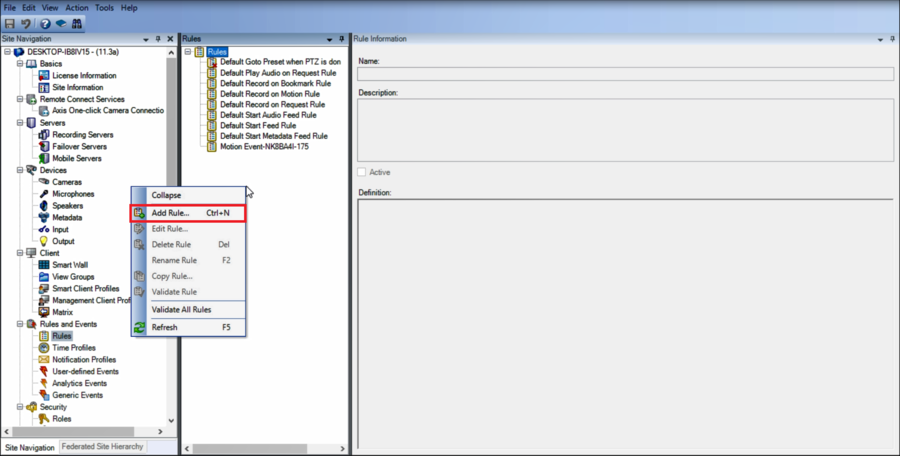
2. Right-click and add a rule
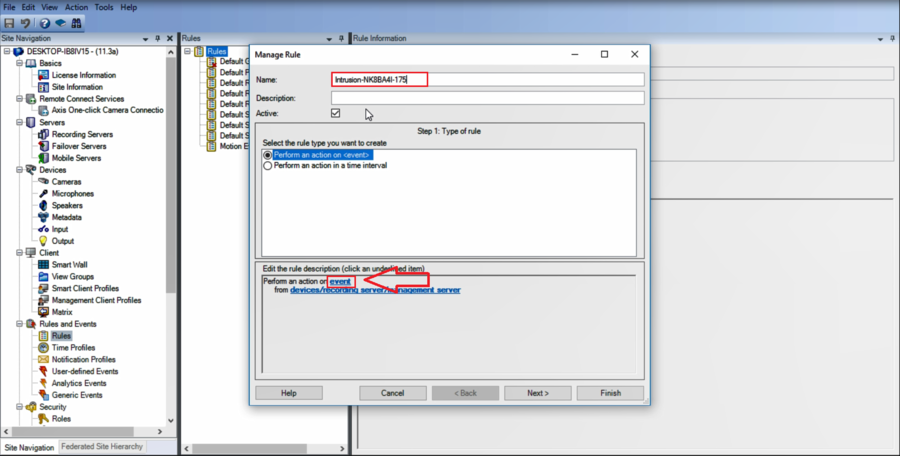
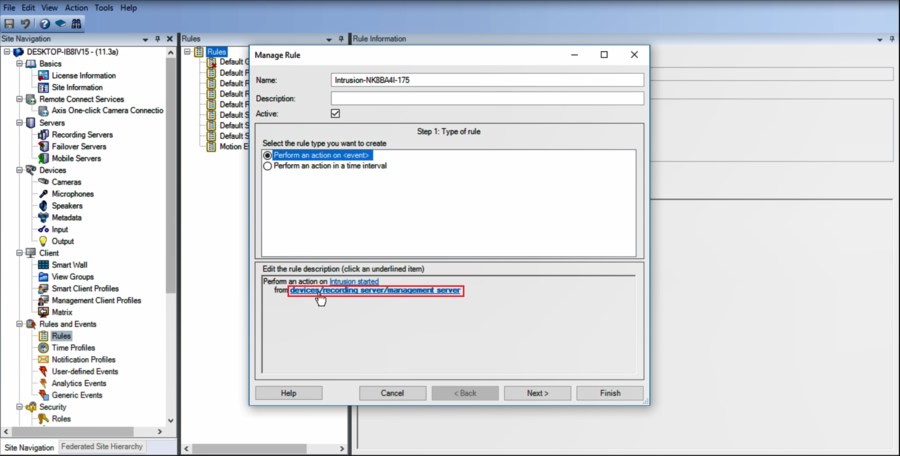
3. Name the new rule and click on even to set an event type
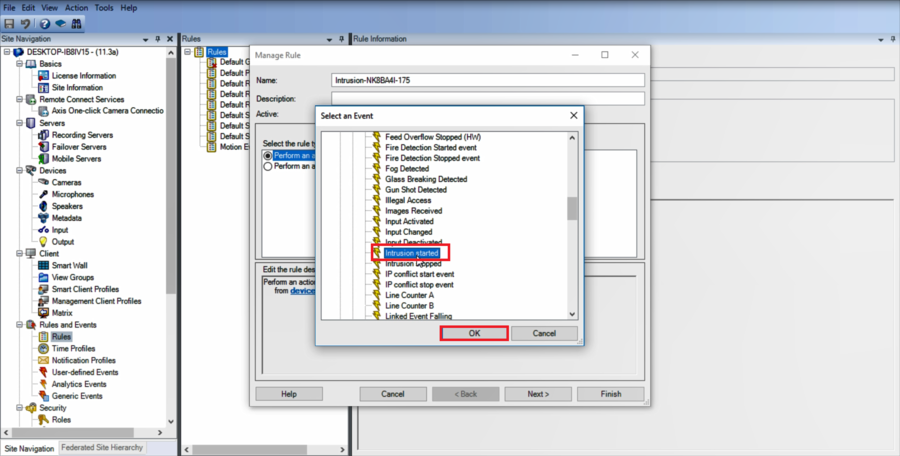
4.Devices>Configurable Events>Intrusion Started and then click on OK
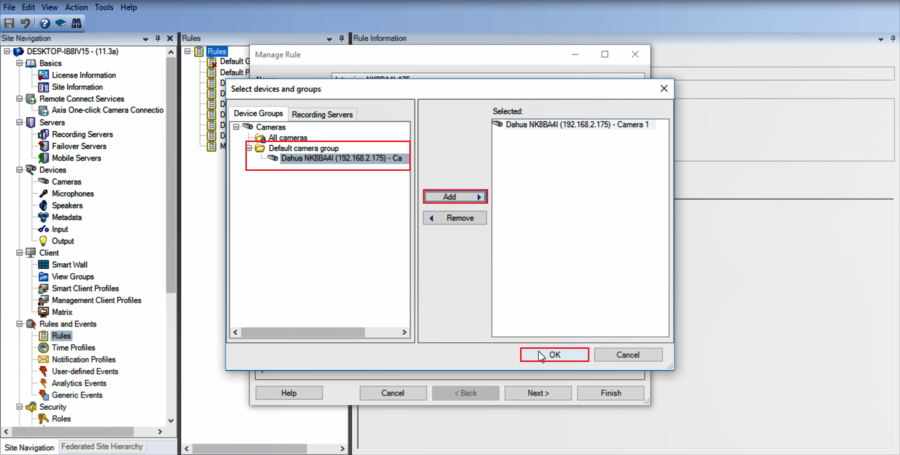
5.Next, we need to add the device
6.Highlight the device>Add>OK> then click on Next to proceed
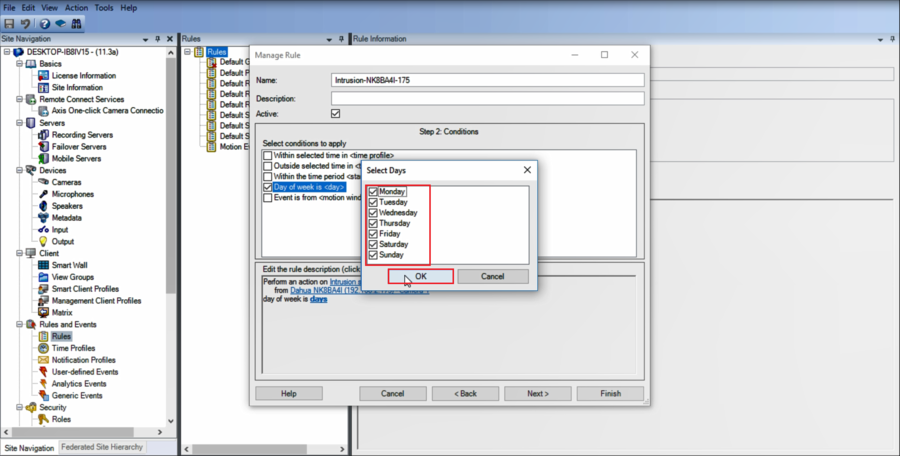
7.Enable "Day of week is" and select the days of the week you want it to be active
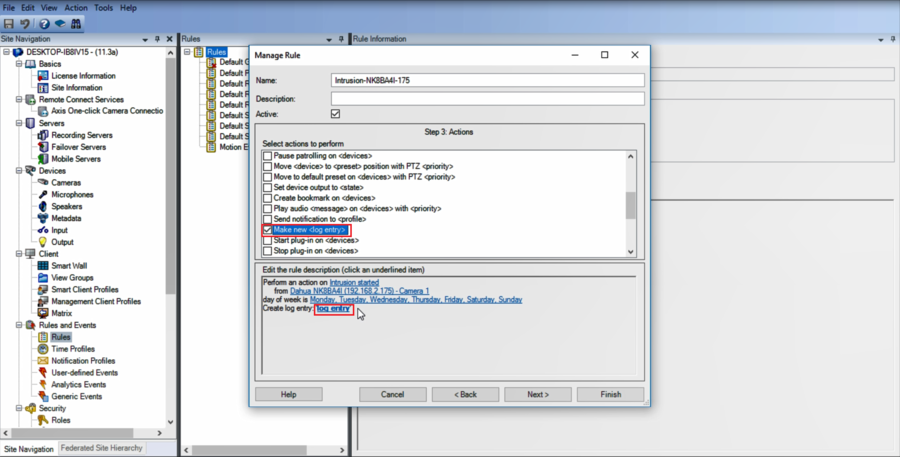
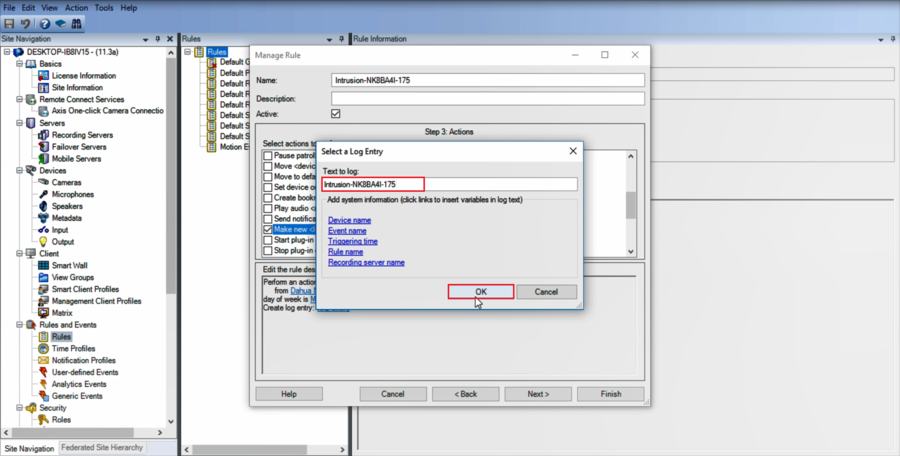
8.Enable "Make a new log" and give it a name, this will help you keep track of when the event was triggered
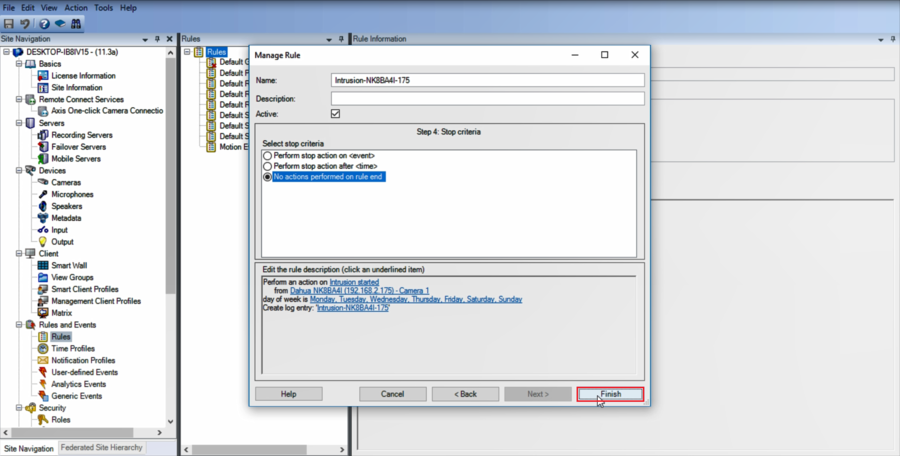
9.Click on Finish to finalize your rule
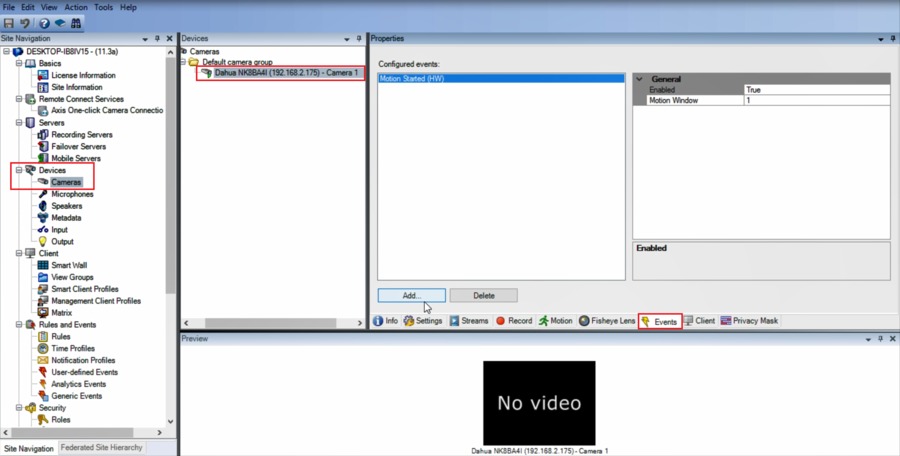
10.Now go to Devices and select your device, click on Event
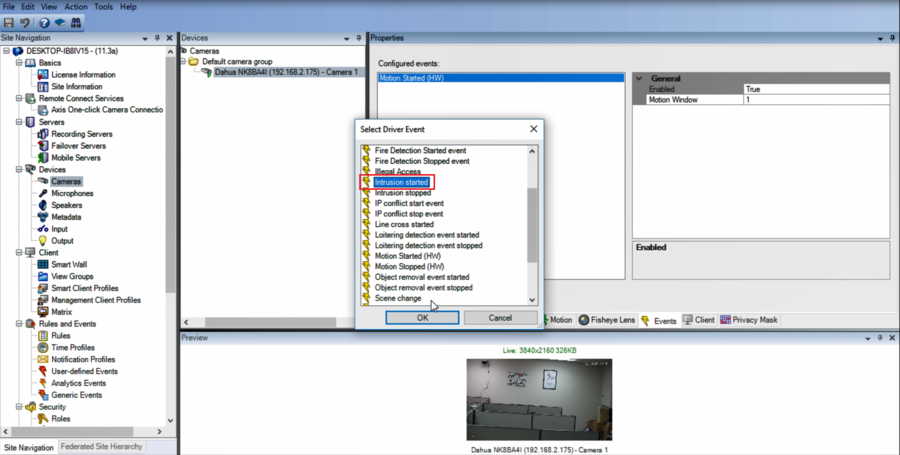
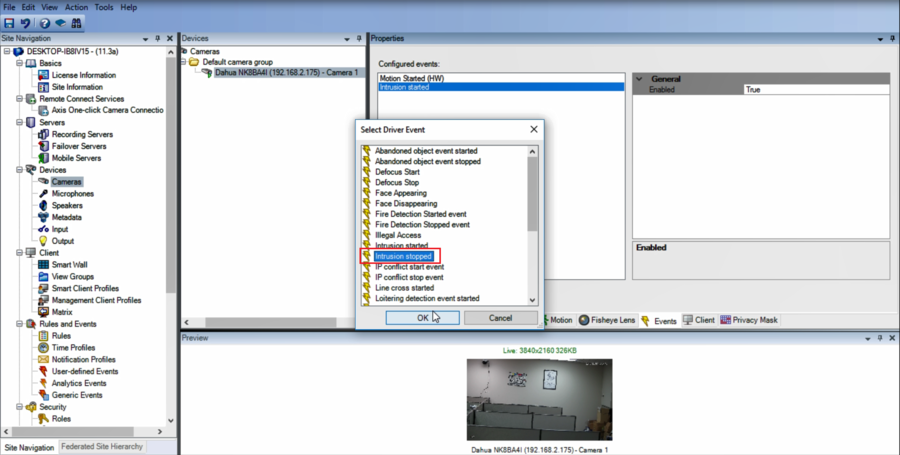
11.Add Intrusion started and Intrusion stopped
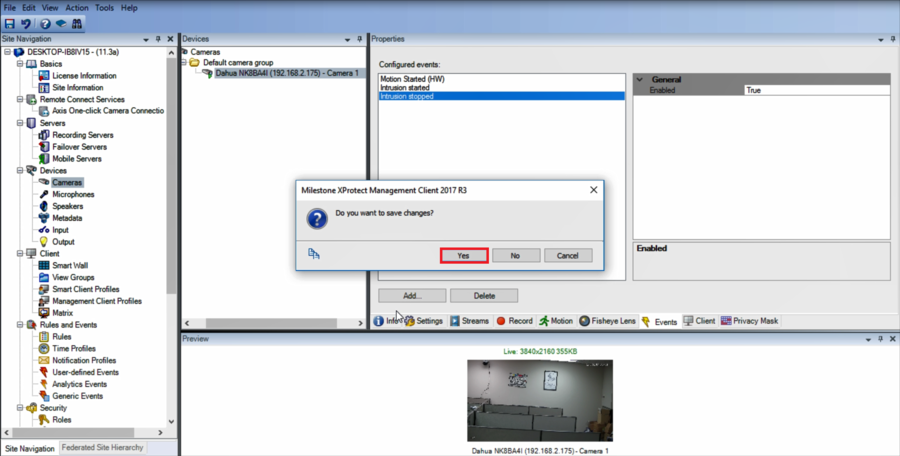
12.Save the changes
13.Go to "Rule Log" to check when the events have been triggered